Do you know HIPAA Compliance?
- There are 43,285 healthcare apps available on the Google Play store in the year 2020.
- 1 in 5 Americans of different age groups tracks their health statistics using an app.
- The global mHealth market is expected to reach $100 billion in 2021, that’s nearly a fivefold increase from around 21 billion dollars in 2016.
The staggering growth in the usage of healthcare apps proves that healthcare efficiency is proportional to healthcare mobilization. It’s because mobile apps have revolutionized the way patients receive medical treatment and get their health status monitored.
It’s great!
However, there exist risks when healthcare practice data or patient data gets stolen. The implications of data breaches have proven very expensive for hospitals or clinics regardless of whether the data is hacked due to employee action, third-party errors or device lost/stolen.
The report states that an upward trend in data breaches observed in the digital healthcare space in the last decade. The breach has resulted in the loss, stolen, or impermissible disclosure of 230,954,151 records which equates to more than 69.78% of the US population.
That’s where HIPAA Compliance regulation comes into the picture.
In 1996, HIPAA was created to set regulatory standards for the healthcare industry where the laws defined the optimal use and management of protected healthcare data. HIPAA compliance is not just deeply ingrained in the healthcare organizations’ DNA, but also applies to the organizations that are dealing with them.
To maintain the integrity and confidentiality of healthcare data, the healthcare entities and the business associates have to implement the technical, physical, and administrative safeguards defined under HIPAA regulation.
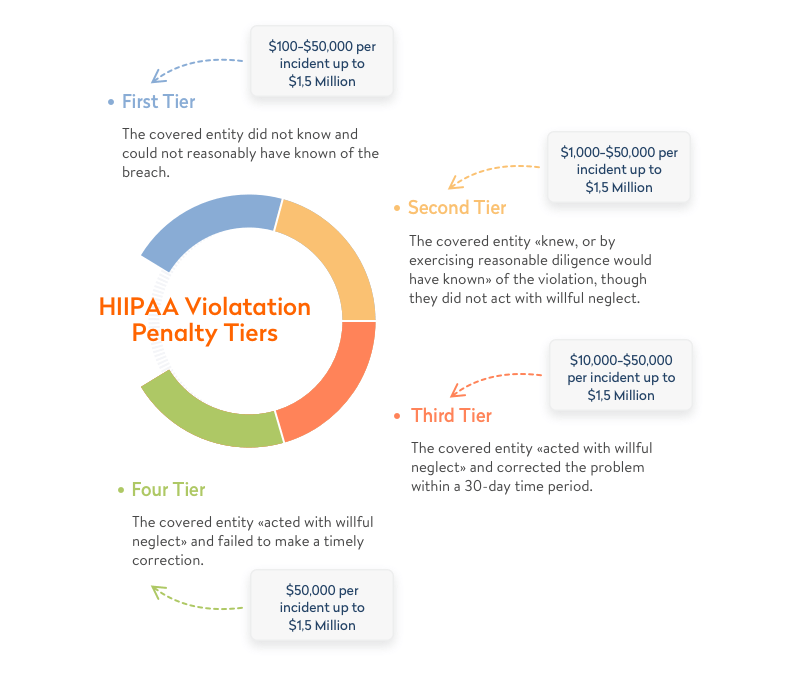
When smartphones and wearables are used to process, send and receive private data, they must comply with HIPAA regulations, else they are subjected to heavy penalties that range from $100 to $50,000 per violation (or per record). Well, the penalties could increase up to $1.5 Million depending on the penalty tier the entity falls into.
Undoubtedly, you want to meet all the safeguards defined under HIPAA to stay HIPAA-compliant. Here’s the checklist we have shared that help you abide by the regulations.
What does the HIPAA Compliance security rule state?

Technical safeguard
The healthcare entity employing the technology needs to follow a few rules to protect and control the data access. In addition to encryption of data in transit or at rest, the companies choose different mechanisms to secure the data.
- Access controls
To restrict the user’s access to the information, the unique user IDs generated for robust authentication of proof of identity. When biometric data, passwords, or smart cards won’t work due to a server down or electric power systems damaged, then a unique way is defined to gain access under such emergencies.
- Audit controls
The developers implement a mechanism where the systems storing data- their activities should be examined and recorded. It helps in analyzing the risk and recommends technical infrastructure to define audit controls.
- Addressable safeguard
The mechanism is created for ePHI authentication, encryption/decryption tools, and automatic logoff. The companies can use the alternative of addressable safeguard or prefer not to implement the safeguards.
Physical safeguard
The safeguard applies to the physical access points where data stored like- remote data centres, on-premise, or in the cloud. It defines how to keep workplaces and smartphone safe and secure from unauthorized access.
- The workstations having access to private data are restricted with the implementation of security systems, door locks, and video surveillance systems.
- For mobile device usage, the users accessing data must follow the defined policies such as deleting all the app’s access authentication details they have when leaving the job.
Administrative safeguard
To monitor employee’s behavior and private data, the privacy and security officers assigned that are liable to check the system against security measures.
- The data usage is analyzed regularly to discover all the security loose points that may result in data breaches and save the app from potential hacks.
- Unauthorized access to private data is prevented by providing access to business entities only after agreement signing.
- Create a data protection integrity plan to make sure a few business processes perform even during contingencies
How can we build a HIPAA-compliant app?
Analyze risk
There is no one-size-fits-all solution to perform risk associated with the data that the company creates, receives, stores, or shares with others. For analyzing the risks and potential threats to the confidentiality and integrity of the data, a couple of things can be done.
It includes identifying where the data is stored and maintained; document the potential risks to data; checking and evaluating current security practices; find out the consequences of the data breach; create an action plan to improve security.
- Make processes conform to HIPAA compliance
When you identify the potential threat in the processes, its time to bring changes in the processes to make it conform to HIPAA compliance.
It starts with employees’ training, where they should be upskilled and up-trained for restricted usage, necessary requirements, data disclosure, two-factor authentication, and cybersecurity measures. It helps in establishing effective network security and showcases the worse consequences of irresponsibly handling critical data.
- Create a long-term strategy
Checking HIPAA compliance is not a one-time process; instead, it’s an ongoing process where a long-term plan is required to monitor and manage the potential risks. In addition to network monitoring software, a couple of tools that detect security threats continuously, analyze audit trails, track logins, automate event analysis and reporting, and perform network event monitoring should be used.
- Data backup
It’s a necessary step that we always keep tabs on. We ensure that our partners (hosting providers) provide recovery and backup services so that data won’t get lost in case of server failure or accidents. During emergencies, the data even if stored somewhere else, then authorized staff can easily access and store the data.
- Maintain integrity
When we build HIPAA-compliant health applications, it’s ensured that infrastructure must set up in a way that data in storage, transition, or collection remain safe and tamper-proof.
Intentionally or unintentionally, if the unauthorized access occurs, it’s detected and reported in the early stage. Also, encryption, backup, access authorization, and restricted physical access to infrastructure are ensured to maintain the integrity of the application.
- Data disposal
Sometimes, the data is archived or backup data gets expired, this data must be removed forever. We take all the precautionary measures while deleting the private data permanently so that the data is impossible to retrieve in the future.
Takeaway
Are you ready to set healthcare space on mobile fire? If so, it’s the best decision you have made that help you enjoy the perks of digitization. After the COVID-19 impact, the healthcare industry is highly focusing on healthcare mobilization. However, HIPAA compliance, in addition to other healthcare-related regulations stays at the heart of mHealth apps. But, making the apps must be HIPAA-compliant is not a piece of cake. A single mistake can make the app falls into jurisdiction or subject to high penalties.
That’s why the HIPAA compliance checklist provided that enables healthcare entities to achieve grandeur success following the mobilization race while staying HIPAA-compliant.